Spotting Social Engineering Scams: GoTeam's Guide to Cybersecurity Red Flags

It’s quite clear that as we advance digitally, staying secure online has become more challenging than ever. With cyber threats constantly evolving, it’s essential for everyone to adopt a proactive approach to cybersecurity. Following our recent Masterclass on Cybersecurity that took place last September 28, 2023, we at GoTeam feel it’s crucial to share this knowledge and awareness amongst our community and the larger industry as well.
Now, let us unveil the real definition of Social Engineering Scams and shed light on the tactics these cybercriminals employ to manipulate individuals into disclosing sensitive information. Also, to help you stay protected, we uniquely crafted a comprehensive guide on how to prevent falling victim to these social engineering scams.
What Are Social Engineering Scams?
As explained in the Interpol’s official website, social engineering scams are refined manipulation techniques where cybercriminals manipulate individuals into releasing sensitive information to which they do not have legal access. Instead of finding software susceptibilities, these criminals exploit human weaknesses – curiosity, fear, and trust.
Moreover, It is crucial to emphasize that these scams come in different forms, like phishing emails, tempting offers, tricking people into restricted areas, and many more. All of these tactics have one goal in common, which is to deceive and take advantage of individuals for illicit gains.
How to Identify the Red Flags?
Recognizing red flags in social engineering scams is not always simple, but knowing what to look for can significantly reduce your risk of falling victim to them. Here are a few of those signs that you can familiarize yourself with.

1. Suspicious Communication Methods
You should keep an eye out for unusual email formats, unexpected phone calls or messages, and unscheduled requests for remote contact. For instance, an email from your company’s CEO asking you to send money via a wire transfer.
2. Pressure Tactics
Bear in mind that scammers often make things seem urgent. They might use statements like “Your account will be deactivated within 24 hours” or “You’ve won a limited-time prize”. These tactics aim to compel immediate action, preventing you from taking the time to consider the request’s legitimacy.

3. Requests for Sensitive Information
One of the major red flags is when a communication asks for sensitive information. Legit or authentic businesses and organizations usually have protocols against asking for sensitive data, such as passwords, social security numbers, or credit card details, over email or phone.

4. Inconsistencies and Grammatical Errors
Professional organizations invest ample resources and time to ensure their communication is impeccable. Scammers, on the other hand, often make mistakes. Start by looking for inconsistencies in logos, email addresses, or websites and grammatical and spelling errors in the text.
The abovementioned signs are crucial in identifying if a cybercriminal has attacked you. Thus, it is essential to understand these red flags to protect yourself from potential harm caused by social engineering fraud. To effectively understand all these red flags, we crafted a detailed example with a guide just for you.
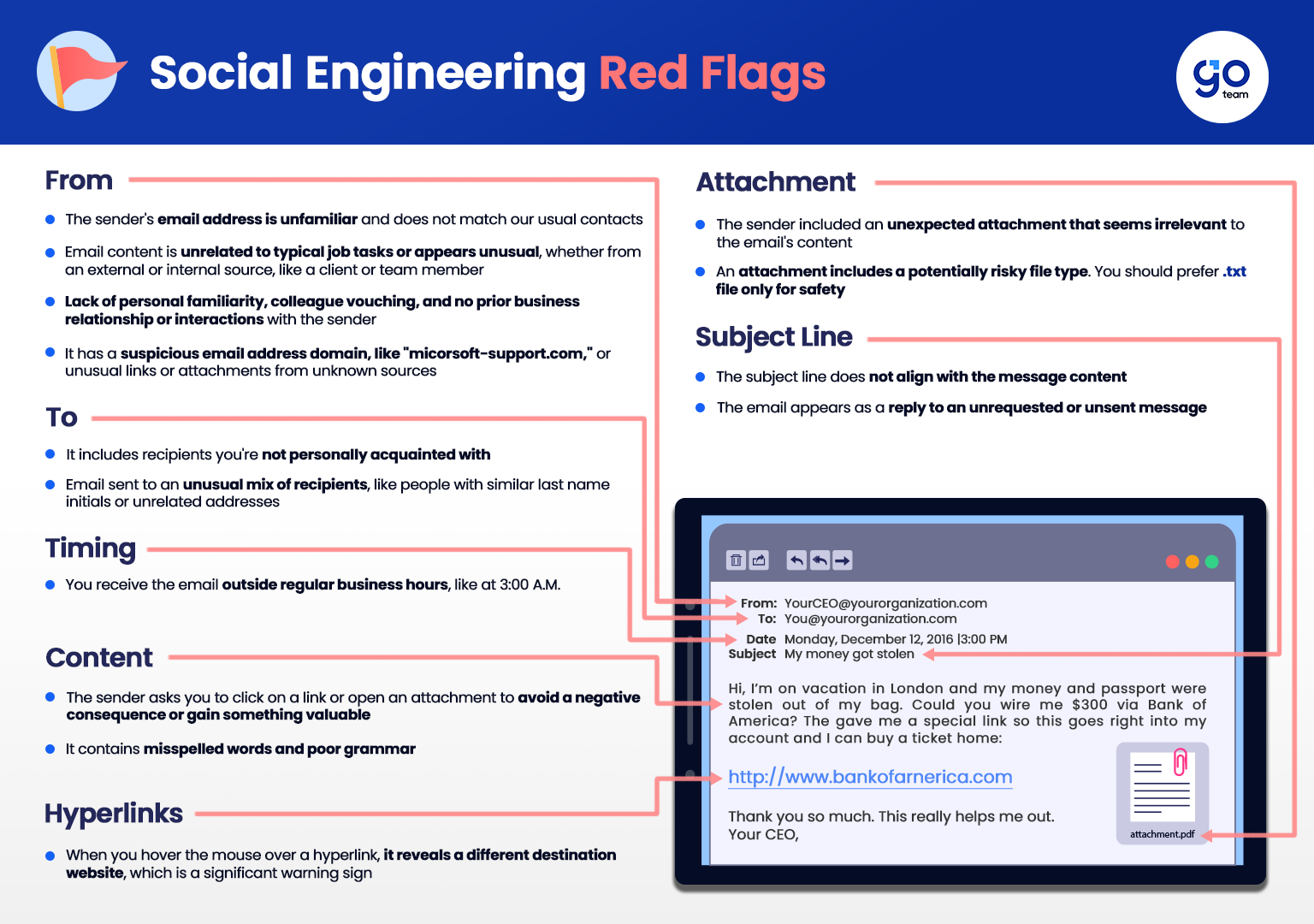
Truly, being aware of the red flags in any online communication and understanding the tactics used by cybercriminals are helpful approaches to combat social engineering scams. Moreover, it is also crucial to stay vigilant, especially when dealing with pressure tactics and requests for sensitive information. Indeed, at GoTeam, ensuring the safety of our clients and team members’ data is our topmost priority because everyone deserves to feel safe. Stay protected, reach out to our team to learn more about our security solutions.

















