Fortify Your Business Against Data Breaches with GoTeam's Cybersecurity & Data Loss Prevention Solutions
On September 22, 2022, one of Australia’s leading telecommunications giants, Optus, found itself at the epicenter of a massive cyber onslaught that sent shockwaves through the nation’s cyber security landscape. As disclosed by Optus, approximately 10 million customers, accounting for nearly 40% of the population, were affected by the cyber-attack. This unprecedented breach has led experts to speculate that it could be Australia’s most severe data breach.
Clearly, this incident is a stark reminder of the critical importance of cyber security and data loss prevention in today’s digital age. Unknowingly to most people, the potential upshots of such breaches extend beyond individual privacy concerns as more aspects of our lives become intertwined with technology.
Here’s where the comprehensive guide on cyber security and data loss prevention becomes essential. This article will delve into the global impacts of data breaches, recent legislation on data leakage in Australia, and our distinct approach and solutions to cyber security and data loss prevention.
GoTeam’s 3 Efficient Pillars for Cyber Security and Data Loss Prevention
At GoTeam, our commitment to your online security is unwavering, especially in today’s dynamic cyber landscape. We devised three functional pillars that would serve as the cornerstone of your digital defence strategy.

Mindset
Keeping data safe is everyone’s responsibility. Recent advancements have introduced novel challenges and strategies to avert data loss, particularly in the sphere of Cyber Security, encompassing both corporate and personal devices and applications.

Skillset
We focus on optimizing skills by managing physical setups for both home and office environments, utilizing corporate devices and approved BYOD containers.
Toolset
The toolset comprises VisualAccess.ai, Teramind, Sophos, ScaleFusion, and Thinscale for various functionalities. These tools contribute to our enhanced approach to managing different aspects efficiently.
Global Effects of Data Breaches
The global effects of data breaches have underscored the critical importance of cyber security in protecting sensitive information. From compromised personal data to financial losses and damaged reputations, understanding these consequences iC/O Ras paramount in strengthening our defences for a secure digital environment. Here are a few more significant effects of data breaches around the globe:
1. Financial Loss
Based on a 2018 study by the Ponemon Institute, data breaches incurred an average cost increase of 6.4%, reaching a range between $3.86 million and $350 million. This upward trend in breach costs organisations’ escalating financial impact in the wake of security incidents.
2. User Privilege Puts Sensitive Data at Risk
User privileges play a critical role in the vulnerability of sensitive data, as indicated by a Cybersecurity Insiders survey of 400,000 online members detailed in The Insider Threat 2018 report. The survey revealed that 37% of respondents had excessive privileges, while 34% had access to sensitive data. This emphasizes the importance of maintaining strict control over user access to mitigate potential risks.
3. Data Leak Incidents are Growing at an Alarming Rate
In 2018, there was a significant surge in data breaches, reaching a reported rate of 57%, over three times higher than the figure from two years before. This 300% increase in breaches highlights the urgent requirement for reinforced security measures to counter this growing threat.
4. IP Losses Due to Cyber Crime is Hurting Companies Globally
McAfee, a well-known American computer security software company, suggests that the United States faces yearly losses of about $12 billion due to cybercrime targeting intellectual property (IP).
These losses are part of a more significant global concern, with projections ranging from $50 billion to $60 billion worldwide. It’s significant to emphasize that the upper limit for annual global IP-related losses is capped at $60 billion.
As these threats grow, it’s clear that data breaches have effects beyond financial implications. The risk of users having too much access and the quick increase in data leaks show that strong cybersecurity is essential to protect sensitive information and keep digital systems safe and reliable.
Real Estate Firm Harcourts Hit by Data Breach
Harcourts, a well-known real estate company, discovered a troubling data breach at its Melbourne City office. This breach has raised severe alarms as it can potentially compromise the confidential information of tenants, landlords, and tradespeople, leaving them vulnerable to cyber threats.
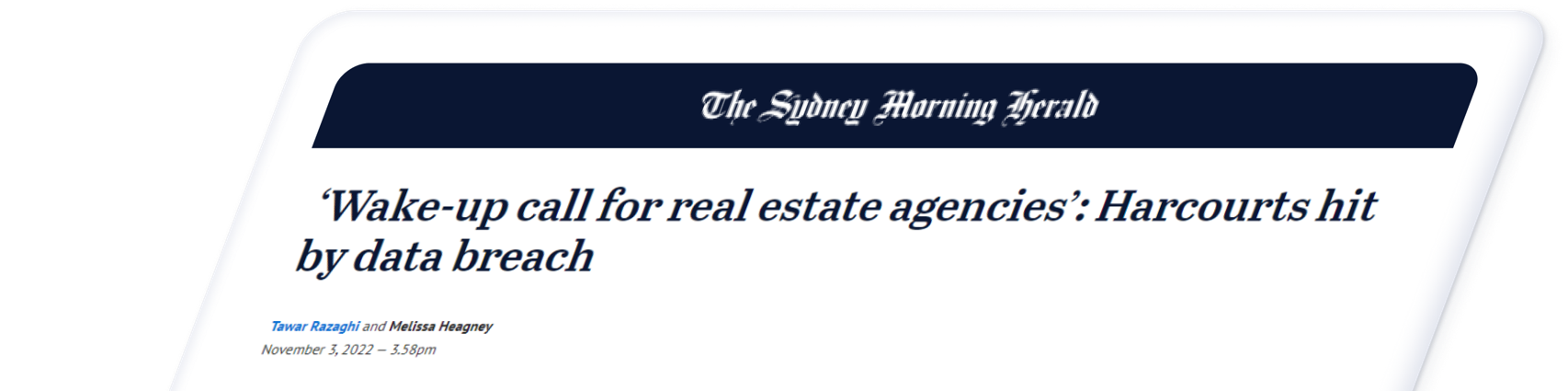
On October 24, 2022, the franchisee learned that someone unauthorised entered their rental property database. Personal information that could have potentially been breached for tenants consisted of names, addresses, email addresses, phone numbers, signatures, and photo identification. This information was disclosed in an email dispatched by the office to its clients and later circulated on the Internet.
This situation arose two weeks after security experts and tenants expressed worries about the industry’s vulnerability to data breaches. Also, the industry collects a lot of information with limited oversight, which is causing concerns.
Furthermore, Harcourts shared that the rental property database was accessed by an unknown third party through a representative from the administrative support service provider Stafflink. The company attributed the incident to a Stafflink representative using their personal device for work tasks instead of using a device provided by the company.
New Australian Legislation: Industries To Face Fines of $50M for Data Breaches
Following the huge data leaks in Australia, the newly enacted legislation imposes substantial penalties for severe or repeated breaches of customer information. It is also imperative to highlight that whether the data leak is intentional or deliberative, the company will still be fine for the damages it caused.
GoTeam: Everyone Deserves to Feel Safe
At GoTeam, we firmly believe that everyone deserves to feel safe – be it our clients or team members. Safety transcends both the physical world and the digital realm, which is why we prioritize data security. Recognizing these threats, we meticulously crafted a distinct approach to cybersecurity that would certainly protect an individual and an organization’s sensitive data.
We understand that negligence from even a single individual can harm the security and trust of many; this is why we ensure stringent protocols and measures to guard our operations against any potential breaches. Thus, our clients and team need to know that their data is safe with us. We are always committed to keeping this trust intact.
Comprehension Data Security at GoTeam - Your IP and Data Safety and Priority
At GoTeam, we are fully committed to ensuring the highest levels of safety and security for your data. As our valued client, your IP and data aren’t just our responsibility but also our top priority. You can trust us to safeguard your vital business information with best practices, stringent processes, and top-tier technologies. Here are nine approaches to data security that GoTeam meticulously instrumented:
1. Guards
Our main office is equipped with 24/7 security personnel presence, maintaining a vigilant watch over the entrance as well as the Level 9 lobby. Moreover, our HIPPA-compliant rooms are under constant security cover, accentuating our commitment to enforcing stringent data security measures at all times.
2. Biometrics and ID
We have implemented robust access control systems in our office premises. The access is controlled via photo IDs, QR Codes, and Biometrics. These measures are in place to ensure that only authorized individuals can access our facilities, thus maintaining the confidentiality and security of our work and data.
3. Desk Location
For GoTeam members working from home, we strongly recommend maintaining a secure room or having a wall behind the desk. This practice aims to prevent unintentional data breaches that occur due to curious eyes. We understand that data security is equally essential in a home office setting. Hence, we encourage our team to take these measures to ensure their workspace is secure from potential visual data breaches.
4. AI-Powered Authorized User Access
We use cutting-edge AI technology to ensure the highest level of data security with VisualAccess.ai. This tool authorizes and verifies user approvals every 2 seconds, providing a powerful real-time protection layer. Below are some of its key specifications:
- Authorized User Access
- Users AI to scan users and check against the facial images stored locally on the device.
- If the user is not recognized, the screen is locked, and that image is set to IT to approve or take action. Please note that our process respects privacy and ensures that admins and other team members cannot view a user’s webcam. Our foremost priority is balancing high security with the utmost respect for personal privacy.
5. Data Loss Prevention

We have implemented Teramind’s 24/7 Always ON AI-Powered Data Loss Prevention Suite, a robust and intelligent system designed to prevent potential data losses. This dynamic tool offers a detailed and efficient monitoring system, providing a second-by-second playback of the last 30 days. This allows us to precisely review actions, behaviors and data transactions whenever necessary.
In addition to this advanced monitoring, our system also focuses on preventing potential data breaches by enforcing restrictive measures such as locking down USB ports, disabling copy-paste functions, and limiting storage access. Here are a few of its essential specifications:
- Always on Mode
- No Agent to select the tasks you are working on
- Update via Dothis.to that will connect your tasks to Teramind

Exploring Teramind
Teramind is a renowned global leader in data security and employee monitoring software. The company was established in 2014, and since then, it has been effectively serving various organizations across diverse industry verticals.
Currently, over 3,500 organizations worldwide benefit from its state-of-the-art software solutions that focus on increasing productivity and ensuring data security. Teramind’s headquarters are located in Miami, Florida, USA. However, its influence extends on a global scale, with sales and support operations that span multiple locations around the world. This global presence ensures that they can effectively cater to the needs of their international client base. Below are some of the esteemed recognitions and achievements of Teramind all around the globe:
- Best Pick 2020, Best for Enterprises, and Top 10 Reviews 2017 Gold Awardee presented by Business.com
- With 4.5 Stars User Reviews recognized by Capterra
- Multiple Awards and Top 10 Ranking honored by Finances Online
- Excellent Ranking recognized by Serchen
- With 4.5 Stars User Review recognized by GetApp
- With 4 Stars User Review recognized by TechRadar
- With 5 Stars, “What our Users Think?” recognized by Crozdesk
Teramind’s Offered Solutions
Teramind’s solutions provide powerful, innovative products that enhance data security and maximize workforce productivity. These strategies tackle vital areas such as Insider Threat detection, Employee Monitoring with activity recording, User behavior analytics, and Data Loss Prevention.
A. Insider Threat Detection and Prevention
This is designed to secure an organization’s data and other critical assets from potential threats within the organization itself.
These threats could come from employees or individuals with inside access to an organization’s network, data, and systems. The threats can be accidental, like a well-intended employee unknowingly clicking a phishing email, or sinister, like a disgruntled employee intentionally leaking sensitive data.
Teramind’s solution identifies such threats in real-time by monitoring and analyzing user behavior. The software does this with the help of Artificial Intelligence (AI), which learns standard user behavior patterns and flags anomalies that could point to insider threats.
B. Privileged User Monitoring
It is a powerful solution designed to oversee and control users’ activities with crucial access to sensitive information or critical systems within an organization.
Teramind’s Privileged User Monitoring offers comprehensive visibility into privileged user activities through advanced, real-time monitoring and auditing features. The software records the actions of privileged users, providing timestamps, screenshots, and keystrokes to give you a complete forensic view of what they are doing. Key features like desktop video recording and live view capabilities allow for proactive and reactive monitoring.
C. Session Recording
This Teramind feature is a dynamic tool that enables comprehensive surveillance and compiling of each activity a user performs within their work session. This includes monitoring web traffic, email correspondence, instant messaging, application use, and even keystroke logging.
Additionally, this attribute records all monitored activities in a detailed video and audio format, offering a visual playback complete with time stamps and user id’s. Not only does this provide a thorough, irrefutable audit trail of user conduct for review, but it also serves as invaluable evidence in the event of disputes or investigations.
D. Data Loss Prevention
This significant feature is a sturdy solution designed to protect sensitive data within an organization from being accessed, utilized, or transferred outside the network without authorization.
Key attributes include content inspection and contextual analysis of transactions, enabling sensitive content detection across network channels and peripheral devices. It also offers an option to use pre-defined or customized classification rules to identify various types of sensitive information, such as credit card numbers, social security details, or confidential project data.
GoTeam’s Difference: Monitoring, Threat Detection, and Data Loss Prevention

GoTeam adopts a proactive approach to monitoring, detecting threats, and preventing data loss. Here are the distinct methods that we utilize:
A. Analyze User Behavior
- Anomaly detection
- Behavior analysis
- Dynamic risk scoring
- Malicious behavior detection
B. Detect Insider Threats
- Implement blocking rules
- Malicious activity detection
- Prevent unauthorized data exfiltration
C. Prevent Data Loss
- Fingerprinting
- Anti-exfiltration thru Clipboard, Files, Emails, IM/Chat and Social Media
D. Performance Audit
- SIEM integration
- Activity forensics
- Full-text search
- API integration
E. Ensure Compliance
- Sensitive content and data masking
- Pre-built compliance rules
- GDPR, HIPAA, PCI-DSS and more
F. Optimize Productivity
- Integrated scheduling
- Activity & task metrics
- Time-limit activities
- Idle-time-control
G. Monitor Employees
- Web
- Social Media
- Text
- Remote control
- Policy enforcement
GoTeam’s Difference: Module Level User Control

A. Session Mining & OCR
- Alert when users see a full CC #
- Count how many times a user saw a sensitive record
- All text is indexed – even images
B. Data Loss Prevention
- Classify data
- Track data
- Behavior analysis
- Full forensic data from any attempt
C. User Activity
- Incoming & outgoing emails
- Local, web, email, USB drives, cloud drives and network file Applications
- Websites
- Keystrokes*
- IM / Chats*
- Printing
- Search engines
- Networking
- Console commands
- Online Meetings
- Audio
D. Visual Screen Recording
- Real-time streaming
- Video playback
- Interact and take control of a desktop
- View or Export recorded files as MP4
E. Privacy Protection
- Control all monitoring functions by keywords, app or time
- Silent or revealed agents
F. Prevention
- Define custom actions for unwanted behavior
- Over 200 rule templates
- Alerting: Passive, to user or block
G. BI Reporting
- Instant. Powerful reports
- Apps & Websites
- Productivity
- Behavior
- Risks
- Time tracking

6. End Point Protection
GoTeam utilizes Sophos End Point Protection. This is a security solution designed to protect computing systems from various threats, including ransomware. It fortifies GoTeam’s cybersecurity framework, safeguarding its intellectual property and the sensitive data entrusted by our clients. Here’s how Sophos and its features can benefit GoTeam:
- Endpoint Protection and Response (EDR)
Effortlessly identify and prioritize potential threats, swiftly pinpoint areas requiring attention, and recognize the systems that might be affected.
- Extended Detection and Response (XDR)
Extend beyond the endpoint by integrating data from various products, enhancing visibility even further.
- Anti-Ransomware
Protection against ransomware files, behavioral analysis to counter ransomware as well as boot record attacks, and automatic recovery of damaged files.
- Deep Learning Technology
Intercept X incorporates artificial intelligence that is capable of identifying both known and unknown malware without the dependency on signatures.
- Exploit Prevention
Counter attackers by obstructing the exploits and strategies employed to disseminate malware, steal credentials, and evade detection.
- Managed Detection and Response (MDR)
Within MDR, a skilled group of threat hunters and response specialists work efficiently to take decisive measures on your behalf, effectively neutralizing even the most intricate threats.
- Active Adversary Mitigations
Active adversary mitigation stops persistence on machines, defends against credential theft, and identifies malicious traffic.
- Central Management
Unify your management of endpoint protection, EDR, XDR and other Sophos solutions under a single console.
- Zero Trust Network Access
Unified ZTNA Solution for Remote Workers, providing secure application access through a single agent and console.
7. Information Security Training
At GoTeam, we implement a comprehensive program designed to educate team members about the significance of data safety and security measures. This training is conducted through two primary approaches:
A. Virtual Instructor-LED Training
This format allows participants to interact with a live instructor remotely. It provides the benefits of traditional classroom learning, including real-time interaction, dynamic content delivery, and immediate feedback, but without geographical limitations. Participants can ask questions, participate in collaborative activities, and more, all under the guidance of a skilled instructor.
B. SCORM Simulations
Sharable Content Object Reference Model (SCORM) is a set of technical standards for e-learning software products. It allows online learning content and Learning Management Systems (LMS) to communicate with each other. SCORM simulations are highly interactive, engaging modules where learners can undertake different tasks in a safe, virtual environment. These modules are accessible at any time and from any location.
Through a combination of these learning methodologies, GoTeam ensures that team members remain up-to-date on information security practices and procedures.
8. Random Testing
We utilize Random Testing as a proactive approach executed by our Cyber Security Team to assess the dependability of our system and the preparedness of our team members against potential cybersecurity threats. Here’s how it works:
8.1. Mock tests are conducted without prior notice. These could include simulated phishing attacks, false malware alerts, or pseudo ransomware attacks. The aim is to mimic real-world attack scenarios as closely as possible.
8.2. During and after these simulated attacks, the Cyber Security Team closely assesses user behavior to gauge how well team members respond. This could involve analyzing how quickly threats are identified, measures taken to mitigate the risk, and how effectively the incident response plan is executed.
8.3. If any shortcomings or areas of improvement are identified, the relevant members or teams are offered specialized cybersecurity training. This customized training aims to strengthen their capabilities, ensure they are better prepared for real-life scenarios, and, ultimately, minimize the risk of breaches.

9. Containerization and Device Management
This approach addresses the comprehensive security and management of our team members’ devices, particularly in the context of Bring Your Own Device (BYOD). Here’s what it entails:
9.1. Containerization
This approach isolates an application or operating system from others on the same device. Each ‘container’ runs under a process that keeps it separate, ensuring that information does not cross from one another. Applying this to mobile devices, containerization secures company data even on personal devices. For instance, threats faced by personal apps do not affect protected work-related apps within the container, thus ensuring data security and privacy.
9.2. Device Management
This involves the administration of mobile devices, like smartphones, tablets, and laptops, mainly when used outside the company’s premises. With Secure Remote Worker and Mobile Device Management, organizations can control and protect their data, monitor and manage device settings, and oversee software updates and password policies.
- ScaleFusion – Mobile device and endpoint management for 360° monitoring and security of your device fleet
9.3. BYOD Licensing
BYOD, or Bring Your Own Device, is a policy that allows team members to use their personal devices for work. With a BYOD license, team members can securely access company data from their personal devices. This offers the convenience of using familiar hardware and accommodates the flexibility that remote working requires.
- ThinScale – A software-only solution that locks down a user’s personal Window device to enable compliant, secure BYOD for remote endpoint environments.
It is also imperative to highlight that combining these methods creates a harmonious blend between team member convenience and crucial data security, empowering GoTeam to operate efficiently and securely, regardless of their location.

Compliance Alerts and Security Checks
Our ongoing compliance alerts and security check systems operate ceaselessly to anticipate potential risks and adapt to regulatory changes. Understanding the significance of being alert and prepared in today’s rapidly evolving digital environment, we proactively monitor, analyze, and address any security threats or compliance concerns that might impact your business. Below are the key details on ScaleFusion’s compliance alerts and security checks:
- Battery Usage
Track the battery status of managed devices and issue alerts whenever the battery falls below the specified level.
- Data Usage
Establish monthly data usage limits for devices and deliver notifications to the devices when these limits are exceeded.
- Geo-fence
Define a time-specific geo-fence for devices. Get notifications whenever a device enters or exits the designated geo-fenced area.
- Security Incidents
Stay informed of any security incidents by scheduling automated emails to keep you up-to-date.
- Inactivity Compliance
Determine a permissible duration for device inactivity. Initiate an automated email alert for all inventory devices registering inactivity beyond this designated period.
- Storage Compliance
Establish a storage limit and automate a notification to be sent out when the device storage is on the verge of reaching its limit.
At GoTeam, we aim to protect your business and seamlessly safeguard your operations against data breaches. Remember, with GoTeam, you are not alone. We stand by our promise to protect, secure and ensure peace of mind for your digital landscape, allowing you to focus on your primary goal – growth. Rest assured, your cybersecurity is our foremost priority. Reach out today to learn more about how we can safeguard your business.

















